Log into the Azure portal. Use the search bar to search for "App Registrations" and navigate there. Create a new App by selecting "+ New registration".
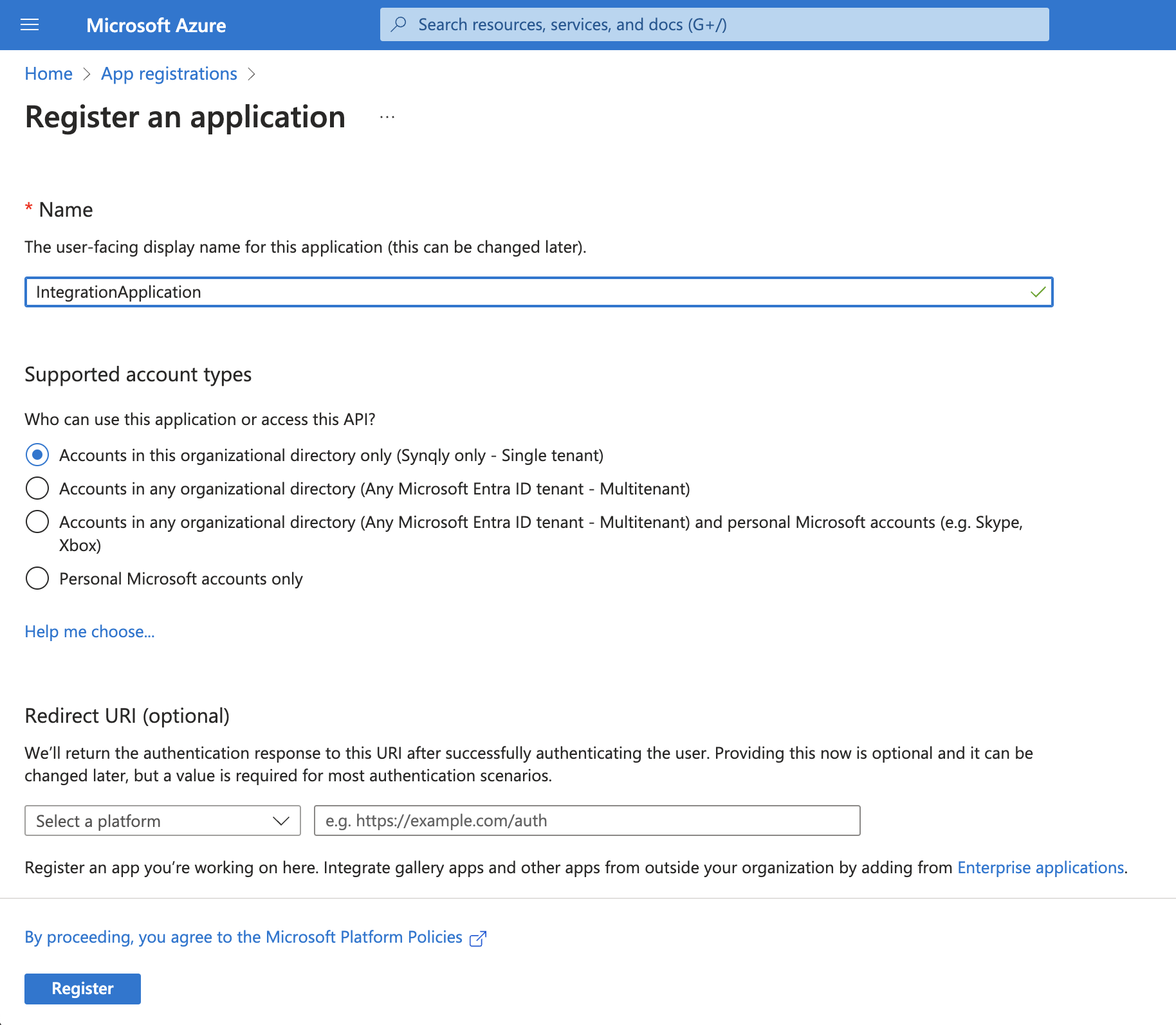
Once you have entered a name for the App, click "Register". This will create the application and generate an "Application (client) ID" and "Directory (tenant) ID". Save these values because you will need them later.
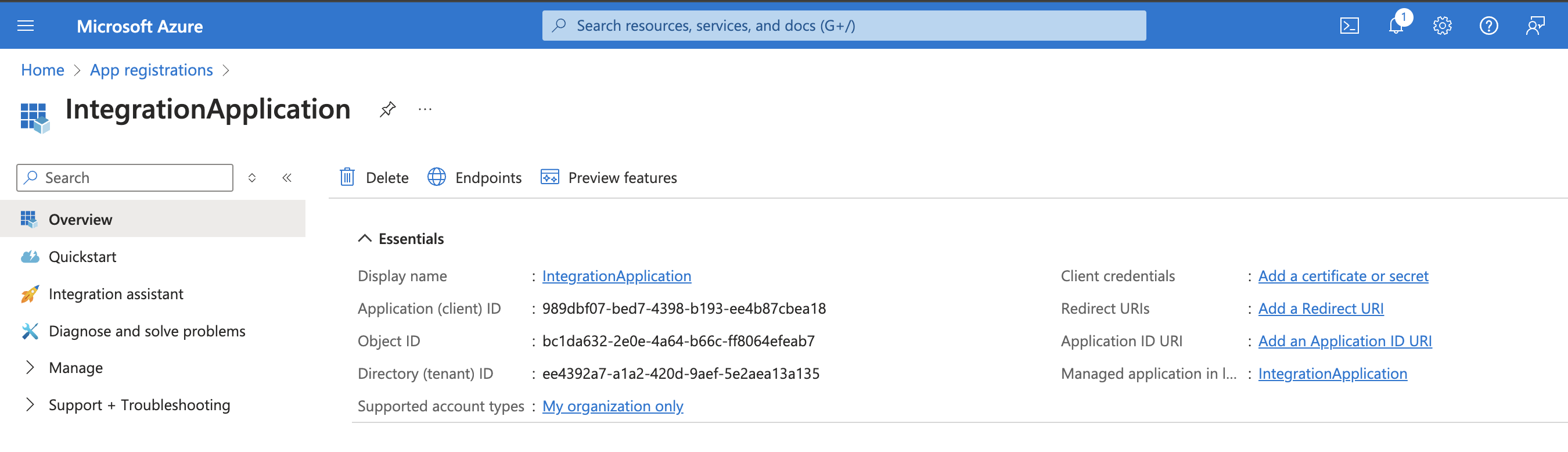
You now need to create an OAuth credential for the App. Under the "Manage" menu, select "Certificates & secrets". Under the "Client secrets" tab, select "+ New client secret". Enter a description and choose an expiration duration, then select the "Add" button.
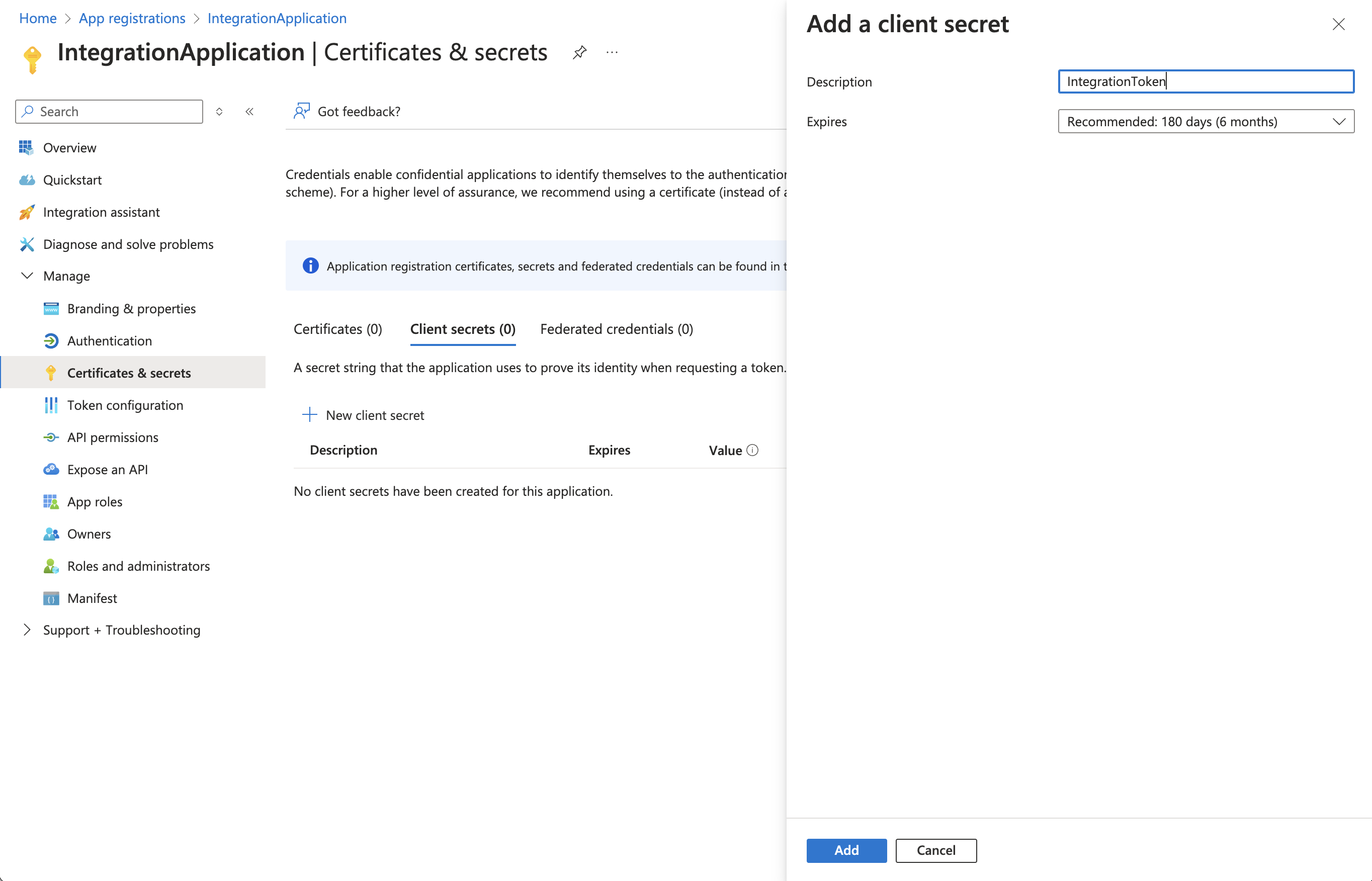
After creating the secret, save the secret "Value". This is the OAuth token secret and you will need this later.
Now that you have an application and credentials for it, you will need to configure Sentinel to receive events.
The first step is to enable Sentinel for a workspace. Search for "Microsoft Sentinel" and go to the Sentinel service. From here, you will either need to select a workspace to add Sentinel to or create a new workspace.
Next search for "Log Analytics workspaces". On this page, select the workspace you just added Sentinel to. When you navigate to "Settings" > "Tables", filter the list to "ASim" and you should see the list of ASim tables. These are the tables Synqly will write to.
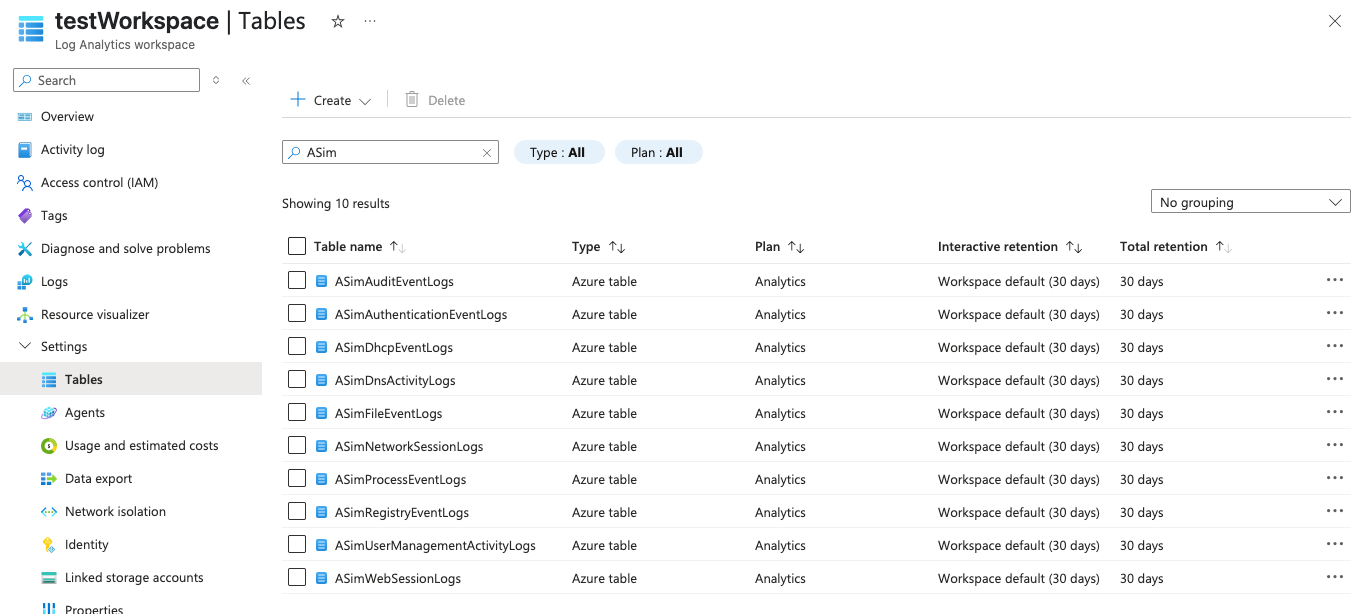
In the Logs Analytics workspace view, open the “JSON View” of this workspace. Save the "Resource ID".
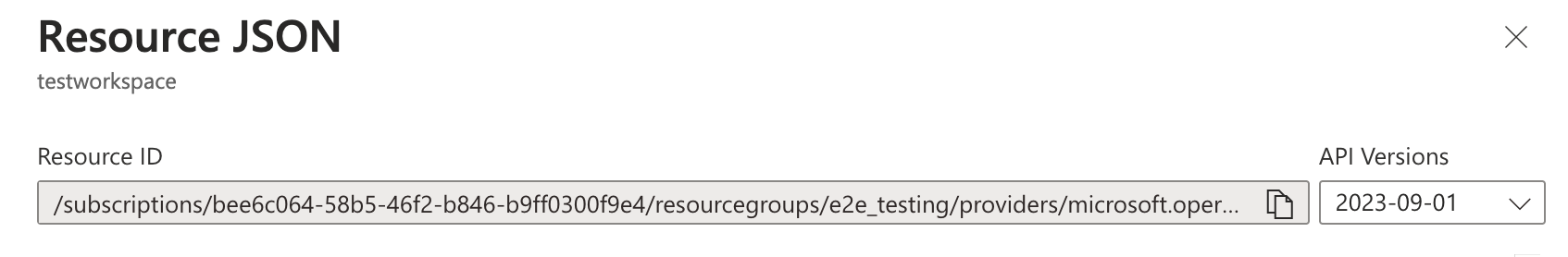
This Resource ID will be used when create a Data Collection Rule below.
We now need a Data Collection Rule (DCR) that creates a pipeline from the data collection API to the ASim tables in Sentinel.
In the Azure search bar, search for "Deploy a custom template". In the Custom deployment service, select "Build your own template in the editor". You will need to copy and paste the template below into the editor.
{
"$schema": "https://schema.management.azure.com/schemas/2019-08-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"parameters": {
"dataCollectionRuleName": {
"type": "string",
"metadata": {
"description": "Specifies the name of the Data Collection Rule to create."
}
},
"workspaceResourceId": {
"type": "string",
"metadata": {
"description": "Specifies the Azure resource ID of the Log Analytics workspace to use. Fully qualified (e.g. /subscriptions/{uuid}/resourcegroups/{name}/providers/microsoft.operationalinsights/workspaces/{workspaceName})"
}
},
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]",
"metadata": {
"description": "Location for all resources."
}
}
},
"variables": {
"streamName": "[concat('Custom-', parameters('dataCollectionRuleName'))]"
},
"resources": [
{
"type": "Microsoft.Insights/dataCollectionRules",
"name": "[parameters('dataCollectionRuleName')]",
"location": "[parameters('location')]",
"apiVersion": "2023-03-11",
"kind": "Direct",
"properties": {
"streamDeclarations": {
"[variables('streamName')]": {
"columns": [
{
"name": "ActingAppId",
"type": "string"
},
{
"name": "ActingAppName",
"type": "string"
},
{
"name": "ActingAppType",
"type": "string"
},
{
"name": "ActingOriginalAppType",
"type": "string"
},
{
"name": "ActingProcessCommandLine",
"type": "string"
},
{
"name": "ActingProcessCreationTime",
"type": "datetime"
},
{
"name": "ActingProcessFileCompany",
"type": "string"
},
{
"name": "ActingProcessFileDescription",
"type": "string"
},
{
"name": "ActingProcessFileInternalName",
"type": "string"
},
{
"name": "ActingProcessFilename",
"type": "string"
},
{
"name": "ActingProcessFileOriginalName",
"type": "string"
},
{
"name": "ActingProcessFileProduct",
"type": "string"
},
{
"name": "ActingProcessFileSize",
"type": "long"
},
{
"name": "ActingProcessFileVersion",
"type": "string"
},
{
"name": "ActingProcessGuid",
"type": "string"
},
{
"name": "ActingProcessId",
"type": "string"
},
{
"name": "ActingProcessIMPHASH",
"type": "string"
},
{
"name": "ActingProcessInjectedAddress",
"type": "string"
},
{
"name": "ActingProcessIntegrityLevel",
"type": "string"
},
{
"name": "ActingProcessIsHidden",
"type": "boolean"
},
{
"name": "ActingProcessMD5",
"type": "string"
},
{
"name": "ActingProcessName",
"type": "string"
},
{
"name": "ActingProcessSHA1",
"type": "string"
},
{
"name": "ActingProcessSHA256",
"type": "string"
},
{
"name": "ActingProcessSHA512",
"type": "string"
},
{
"name": "ActingProcessTokenElevation",
"type": "string"
},
{
"name": "ActorOriginalUserType",
"type": "string"
},
{
"name": "ActorScope",
"type": "string"
},
{
"name": "ActorScopeId",
"type": "string"
},
{
"name": "ActorSessionId",
"type": "string"
},
{
"name": "ActorUserAadId",
"type": "string"
},
{
"name": "ActorUserId",
"type": "string"
},
{
"name": "ActorUserIdType",
"type": "string"
},
{
"name": "ActorUsername",
"type": "string"
},
{
"name": "ActorUsernameType",
"type": "string"
},
{
"name": "ActorUserSid",
"type": "string"
},
{
"name": "ActorUserType",
"type": "string"
},
{
"name": "AdditionalFields",
"type": "dynamic"
},
{
"name": "DhcpCircuitId",
"type": "string"
},
{
"name": "DhcpLeaseDuration",
"type": "int"
},
{
"name": "DhcpSessionDuration",
"type": "int"
},
{
"name": "DhcpSessionId",
"type": "string"
},
{
"name": "DhcpSrcDHCId",
"type": "string"
},
{
"name": "DhcpSubscriberId",
"type": "string"
},
{
"name": "DhcpUserClass",
"type": "string"
},
{
"name": "DhcpUserClassId",
"type": "string"
},
{
"name": "DhcpVendorClass",
"type": "string"
},
{
"name": "DhcpVendorClassId",
"type": "string"
},
{
"name": "DnsFlags",
"type": "string"
},
{
"name": "DnsFlagsAuthenticated",
"type": "boolean"
},
{
"name": "DnsFlagsAuthoritative",
"type": "boolean"
},
{
"name": "DnsFlagsCheckingDisabled",
"type": "boolean"
},
{
"name": "DnsFlagsRecursionAvailable",
"type": "boolean"
},
{
"name": "DnsFlagsRecursionDesired",
"type": "boolean"
},
{
"name": "DnsFlagsTruncated",
"type": "boolean"
},
{
"name": "DnsFlagsZ",
"type": "boolean"
},
{
"name": "DnsNetworkDuration",
"type": "int"
},
{
"name": "DnsQuery",
"type": "string"
},
{
"name": "DnsQueryClass",
"type": "int"
},
{
"name": "DnsQueryClassName",
"type": "string"
},
{
"name": "DnsQueryType",
"type": "int"
},
{
"name": "DnsQueryTypeName",
"type": "string"
},
{
"name": "DnsResponseCode",
"type": "int"
},
{
"name": "DnsResponseIpCity",
"type": "string"
},
{
"name": "DnsResponseIpCountry",
"type": "string"
},
{
"name": "DnsResponseIpLatitude",
"type": "real"
},
{
"name": "DnsResponseIpLongitude",
"type": "real"
},
{
"name": "DnsResponseIpRegion",
"type": "string"
},
{
"name": "DnsResponseName",
"type": "string"
},
{
"name": "DnsSessionId",
"type": "string"
},
{
"name": "Dst",
"type": "string"
},
{
"name": "DstAppId",
"type": "string"
},
{
"name": "DstAppName",
"type": "string"
},
{
"name": "DstAppType",
"type": "string"
},
{
"name": "DstBytes",
"type": "long"
},
{
"name": "DstDescription",
"type": "string"
},
{
"name": "DstDeviceType",
"type": "string"
},
{
"name": "DstDomain",
"type": "string"
},
{
"name": "DstDomainType",
"type": "string"
},
{
"name": "DstDvcId",
"type": "string"
},
{
"name": "DstDvcIdType",
"type": "string"
},
{
"name": "DstDvcScope",
"type": "string"
},
{
"name": "DstDvcScopeId",
"type": "string"
},
{
"name": "DstFQDN",
"type": "string"
},
{
"name": "DstGeoCity",
"type": "string"
},
{
"name": "DstGeoCountry",
"type": "string"
},
{
"name": "DstGeoLatitude",
"type": "real"
},
{
"name": "DstGeoLongitude",
"type": "real"
},
{
"name": "DstGeoRegion",
"type": "string"
},
{
"name": "DstHostname",
"type": "string"
},
{
"name": "DstInterfaceGuid",
"type": "string"
},
{
"name": "DstInterfaceName",
"type": "string"
},
{
"name": "DstIpAddr",
"type": "string"
},
{
"name": "DstMacAddr",
"type": "string"
},
{
"name": "DstNatIpAddr",
"type": "string"
},
{
"name": "DstNatPortNumber",
"type": "int"
},
{
"name": "DstOriginalRiskLevel",
"type": "string"
},
{
"name": "DstOriginalUserType",
"type": "string"
},
{
"name": "DstPackets",
"type": "long"
},
{
"name": "DstPortNumber",
"type": "int"
},
{
"name": "DstRiskLevel",
"type": "int"
},
{
"name": "DstSubscriptionId",
"type": "string"
},
{
"name": "DstUserId",
"type": "string"
},
{
"name": "DstUserIdType",
"type": "string"
},
{
"name": "DstUsername",
"type": "string"
},
{
"name": "DstUsernameType",
"type": "string"
},
{
"name": "DstUserType",
"type": "string"
},
{
"name": "DstVlanId",
"type": "string"
},
{
"name": "DstZone",
"type": "string"
},
{
"name": "Dvc",
"type": "string"
},
{
"name": "DvcAction",
"type": "string"
},
{
"name": "DvcDescription",
"type": "string"
},
{
"name": "DvcDomain",
"type": "string"
},
{
"name": "DvcDomainType",
"type": "string"
},
{
"name": "DvcFQDN",
"type": "string"
},
{
"name": "DvcHostname",
"type": "string"
},
{
"name": "DvcId",
"type": "string"
},
{
"name": "DvcIdType",
"type": "string"
},
{
"name": "DvcInboundInterface",
"type": "string"
},
{
"name": "DvcInterface",
"type": "string"
},
{
"name": "DvcIpAddr",
"type": "string"
},
{
"name": "DvcMacAddr",
"type": "string"
},
{
"name": "DvcOriginalAction",
"type": "string"
},
{
"name": "DvcOs",
"type": "string"
},
{
"name": "DvcOsVersion",
"type": "string"
},
{
"name": "DvcOutboundInterface",
"type": "string"
},
{
"name": "DvcScope",
"type": "string"
},
{
"name": "DvcScopeId",
"type": "string"
},
{
"name": "DvcSubscriptionId",
"type": "string"
},
{
"name": "DvcZone",
"type": "string"
},
{
"name": "EventCount",
"type": "int"
},
{
"name": "EventEndTime",
"type": "datetime"
},
{
"name": "EventMessage",
"type": "string"
},
{
"name": "EventOriginalResultDetails",
"type": "string"
},
{
"name": "EventOriginalSeverity",
"type": "string"
},
{
"name": "EventOriginalSubType",
"type": "string"
},
{
"name": "EventOriginalType",
"type": "string"
},
{
"name": "EventOriginalUid",
"type": "string"
},
{
"name": "EventOwner",
"type": "string"
},
{
"name": "EventProduct",
"type": "string"
},
{
"name": "EventProductVersion",
"type": "string"
},
{
"name": "EventReportUrl",
"type": "string"
},
{
"name": "EventResult",
"type": "string"
},
{
"name": "EventResultDetails",
"type": "string"
},
{
"name": "EventSchema",
"type": "string"
},
{
"name": "EventSchemaVersion",
"type": "string"
},
{
"name": "EventSeverity",
"type": "string"
},
{
"name": "EventStartTime",
"type": "datetime"
},
{
"name": "EventSubType",
"type": "string"
},
{
"name": "EventType",
"type": "string"
},
{
"name": "EventVendor",
"type": "string"
},
{
"name": "FileContentType",
"type": "string"
},
{
"name": "FileMD5",
"type": "string"
},
{
"name": "FileName",
"type": "string"
},
{
"name": "FileSHA1",
"type": "string"
},
{
"name": "FileSHA256",
"type": "string"
},
{
"name": "FileSHA512",
"type": "string"
},
{
"name": "FileSize",
"type": "int"
},
{
"name": "GroupId",
"type": "string"
},
{
"name": "GroupIdType",
"type": "string"
},
{
"name": "GroupName",
"type": "string"
},
{
"name": "GroupNameType",
"type": "string"
},
{
"name": "GroupOriginalType",
"type": "string"
},
{
"name": "GroupType",
"type": "string"
},
{
"name": "HashType",
"type": "string"
},
{
"name": "HttpContentFormat",
"type": "string"
},
{
"name": "HttpContentType",
"type": "string"
},
{
"name": "HttpHost",
"type": "string"
},
{
"name": "HttpReferrer",
"type": "string"
},
{
"name": "HttpRequestMethod",
"type": "string"
},
{
"name": "HttpRequestTime",
"type": "int"
},
{
"name": "HttpRequestXff",
"type": "string"
},
{
"name": "HttpResponseTime",
"type": "int"
},
{
"name": "HttpUserAgent",
"type": "string"
},
{
"name": "HttpVersion",
"type": "string"
},
{
"name": "LogonMethod",
"type": "string"
},
{
"name": "LogonProtocol",
"type": "string"
},
{
"name": "NetworkApplicationProtocol",
"type": "string"
},
{
"name": "NetworkBytes",
"type": "long"
},
{
"name": "NetworkConnectionHistory",
"type": "string"
},
{
"name": "NetworkDirection",
"type": "string"
},
{
"name": "NetworkDuration",
"type": "int"
},
{
"name": "NetworkIcmpCode",
"type": "int"
},
{
"name": "NetworkIcmpType",
"type": "string"
},
{
"name": "NetworkPackets",
"type": "long"
},
{
"name": "NetworkProtocol",
"type": "string"
},
{
"name": "NetworkProtocolVersion",
"type": "string"
},
{
"name": "NetworkRuleName",
"type": "string"
},
{
"name": "NetworkRuleNumber",
"type": "int"
},
{
"name": "NetworkSessionId",
"type": "string"
},
{
"name": "NewPropertyValue",
"type": "string"
},
{
"name": "NewValue",
"type": "string"
},
{
"name": "Object",
"type": "string"
},
{
"name": "ObjectId",
"type": "string"
},
{
"name": "ObjectType",
"type": "string"
},
{
"name": "OldValue",
"type": "string"
},
{
"name": "Operation",
"type": "string"
},
{
"name": "OriginalObjectType",
"type": "string"
},
{
"name": "ParentProcessCommandLine",
"type": "string"
},
{
"name": "ParentProcessCreationTime",
"type": "datetime"
},
{
"name": "ParentProcessFileCompany",
"type": "string"
},
{
"name": "ParentProcessFileDescription",
"type": "string"
},
{
"name": "ParentProcessFileProduct",
"type": "string"
},
{
"name": "ParentProcessFileVersion",
"type": "string"
},
{
"name": "ParentProcessGuid",
"type": "string"
},
{
"name": "ParentProcessId",
"type": "string"
},
{
"name": "ParentProcessIMPHASH",
"type": "string"
},
{
"name": "ParentProcessInjectedAddress",
"type": "string"
},
{
"name": "ParentProcessIntegrityLevel",
"type": "string"
},
{
"name": "ParentProcessIsHidden",
"type": "boolean"
},
{
"name": "ParentProcessMD5",
"type": "string"
},
{
"name": "ParentProcessName",
"type": "string"
},
{
"name": "ParentProcessSHA1",
"type": "string"
},
{
"name": "ParentProcessSHA256",
"type": "string"
},
{
"name": "ParentProcessSHA512",
"type": "string"
},
{
"name": "ParentProcessTokenElevation",
"type": "string"
},
{
"name": "PreviousPropertyValue",
"type": "string"
},
{
"name": "RegistryKey",
"type": "string"
},
{
"name": "RegistryPreviousKey",
"type": "string"
},
{
"name": "RegistryPreviousValue",
"type": "string"
},
{
"name": "RegistryPreviousValueData",
"type": "string"
},
{
"name": "RegistryPreviousValueType",
"type": "string"
},
{
"name": "RegistryValue",
"type": "string"
},
{
"name": "RegistryValueData",
"type": "string"
},
{
"name": "RegistryValueType",
"type": "string"
},
{
"name": "RequestedIpAddr",
"type": "string"
},
{
"name": "Rule",
"type": "string"
},
{
"name": "RuleName",
"type": "string"
},
{
"name": "RuleNumber",
"type": "int"
},
{
"name": "SourceSystem",
"type": "string"
},
{
"name": "Src",
"type": "string"
},
{
"name": "SrcAppId",
"type": "string"
},
{
"name": "SrcAppName",
"type": "string"
},
{
"name": "SrcAppType",
"type": "string"
},
{
"name": "SrcBytes",
"type": "long"
},
{
"name": "SrcDescription",
"type": "string"
},
{
"name": "SrcDeviceType",
"type": "string"
},
{
"name": "SrcDomain",
"type": "string"
},
{
"name": "SrcDomainType",
"type": "string"
},
{
"name": "SrcDvcId",
"type": "string"
},
{
"name": "SrcDvcIdType",
"type": "string"
},
{
"name": "SrcDvcOs",
"type": "string"
},
{
"name": "SrcDvcScope",
"type": "string"
},
{
"name": "SrcDvcScopeId",
"type": "string"
},
{
"name": "SrcFileCreationTime",
"type": "datetime"
},
{
"name": "SrcFileDirectory",
"type": "string"
},
{
"name": "SrcFileExtension",
"type": "string"
},
{
"name": "SrcFileMD5",
"type": "string"
},
{
"name": "SrcFileMimeType",
"type": "string"
},
{
"name": "SrcFileName",
"type": "string"
},
{
"name": "SrcFilePath",
"type": "string"
},
{
"name": "SrcFilePathType",
"type": "string"
},
{
"name": "SrcFileSHA1",
"type": "string"
},
{
"name": "SrcFileSHA256",
"type": "string"
},
{
"name": "SrcFileSHA512",
"type": "string"
},
{
"name": "SrcFileSize",
"type": "long"
},
{
"name": "SrcFQDN",
"type": "string"
},
{
"name": "SrcGeoCity",
"type": "string"
},
{
"name": "SrcGeoCountry",
"type": "string"
},
{
"name": "SrcGeoLatitude",
"type": "real"
},
{
"name": "SrcGeoLongitude",
"type": "real"
},
{
"name": "SrcGeoRegion",
"type": "string"
},
{
"name": "SrcHostname",
"type": "string"
},
{
"name": "SrcInterfaceGuid",
"type": "string"
},
{
"name": "SrcInterfaceName",
"type": "string"
},
{
"name": "SrcIpAddr",
"type": "string"
},
{
"name": "SrcIsp",
"type": "string"
},
{
"name": "SrcMacAddr",
"type": "string"
},
{
"name": "SrcNatIpAddr",
"type": "string"
},
{
"name": "SrcNatPortNumber",
"type": "int"
},
{
"name": "SrcOriginalRiskLevel",
"type": "string"
},
{
"name": "SrcOriginalUserType",
"type": "string"
},
{
"name": "SrcPackets",
"type": "long"
},
{
"name": "SrcPortNumber",
"type": "int"
},
{
"name": "SrcProcessGuid",
"type": "string"
},
{
"name": "SrcProcessId",
"type": "string"
},
{
"name": "SrcProcessName",
"type": "string"
},
{
"name": "SrcRiskLevel",
"type": "int"
},
{
"name": "SrcSubscriptionId",
"type": "string"
},
{
"name": "SrcUserId",
"type": "string"
},
{
"name": "SrcUserIdType",
"type": "string"
},
{
"name": "SrcUsername",
"type": "string"
},
{
"name": "SrcUsernameType",
"type": "string"
},
{
"name": "SrcUserScope",
"type": "string"
},
{
"name": "SrcUserScopeId",
"type": "string"
},
{
"name": "SrcUserSessionId",
"type": "string"
},
{
"name": "SrcUserType",
"type": "string"
},
{
"name": "SrcUserUid",
"type": "string"
},
{
"name": "SrcVlanId",
"type": "string"
},
{
"name": "SrcZone",
"type": "string"
},
{
"name": "TargetAppId",
"type": "string"
},
{
"name": "TargetAppName",
"type": "string"
},
{
"name": "TargetAppType",
"type": "string"
},
{
"name": "TargetDescription",
"type": "string"
},
{
"name": "TargetDeviceType",
"type": "string"
},
{
"name": "TargetDomain",
"type": "string"
},
{
"name": "TargetDomainType",
"type": "string"
},
{
"name": "TargetDvcId",
"type": "string"
},
{
"name": "TargetDvcIdType",
"type": "string"
},
{
"name": "TargetDvcOs",
"type": "string"
},
{
"name": "TargetDvcScope",
"type": "string"
},
{
"name": "TargetDvcScopeId",
"type": "string"
},
{
"name": "TargetFileCreationTime",
"type": "datetime"
},
{
"name": "TargetFileDirectory",
"type": "string"
},
{
"name": "TargetFileExtension",
"type": "string"
},
{
"name": "TargetFileMD5",
"type": "string"
},
{
"name": "TargetFileMimeType",
"type": "string"
},
{
"name": "TargetFileName",
"type": "string"
},
{
"name": "TargetFilePath",
"type": "string"
},
{
"name": "TargetFilePathType",
"type": "string"
},
{
"name": "TargetFileSHA1",
"type": "string"
},
{
"name": "TargetFileSHA256",
"type": "string"
},
{
"name": "TargetFileSHA512",
"type": "string"
},
{
"name": "TargetFileSize",
"type": "long"
},
{
"name": "TargetFQDN",
"type": "string"
},
{
"name": "TargetGeoCity",
"type": "string"
},
{
"name": "TargetGeoCountry",
"type": "string"
},
{
"name": "TargetGeoLatitude",
"type": "real"
},
{
"name": "TargetGeoLongitude",
"type": "real"
},
{
"name": "TargetGeoRegion",
"type": "string"
},
{
"name": "TargetHostname",
"type": "string"
},
{
"name": "TargetIpAddr",
"type": "string"
},
{
"name": "TargetOriginalAppType",
"type": "string"
},
{
"name": "TargetOriginalRiskLevel",
"type": "string"
},
{
"name": "TargetOriginalUserType",
"type": "string"
},
{
"name": "TargetPortNumber",
"type": "int"
},
{
"name": "TargetProcessCommandLine",
"type": "string"
},
{
"name": "TargetProcessCreationTime",
"type": "datetime"
},
{
"name": "TargetProcessCurrentDirectory",
"type": "string"
},
{
"name": "TargetProcessFileCompany",
"type": "string"
},
{
"name": "TargetProcessFileDescription",
"type": "string"
},
{
"name": "TargetProcessFileInternalName",
"type": "string"
},
{
"name": "TargetProcessFilename",
"type": "string"
},
{
"name": "TargetProcessFileOriginalName",
"type": "string"
},
{
"name": "TargetProcessFileProduct",
"type": "string"
},
{
"name": "TargetProcessFileSize",
"type": "long"
},
{
"name": "TargetProcessFileVersion",
"type": "string"
},
{
"name": "TargetProcessGuid",
"type": "string"
},
{
"name": "TargetProcessId",
"type": "string"
},
{
"name": "TargetProcessIMPHASH",
"type": "string"
},
{
"name": "TargetProcessInjectedAddress",
"type": "string"
},
{
"name": "TargetProcessIntegrityLevel",
"type": "string"
},
{
"name": "TargetProcessIsHidden",
"type": "boolean"
},
{
"name": "TargetProcessMD5",
"type": "string"
},
{
"name": "TargetProcessName",
"type": "string"
},
{
"name": "TargetProcessSHA1",
"type": "string"
},
{
"name": "TargetProcessSHA256",
"type": "string"
},
{
"name": "TargetProcessSHA512",
"type": "string"
},
{
"name": "TargetProcessStatusCode",
"type": "string"
},
{
"name": "TargetProcessTokenElevation",
"type": "string"
},
{
"name": "TargetRiskLevel",
"type": "int"
},
{
"name": "TargetScope",
"type": "string"
},
{
"name": "TargetScopeId",
"type": "string"
},
{
"name": "TargetSessionId",
"type": "string"
},
{
"name": "TargetUrl",
"type": "string"
},
{
"name": "TargetUserId",
"type": "string"
},
{
"name": "TargetUserIdType",
"type": "string"
},
{
"name": "TargetUsername",
"type": "string"
},
{
"name": "TargetUsernameType",
"type": "string"
},
{
"name": "TargetUserScope",
"type": "string"
},
{
"name": "TargetUserScopeId",
"type": "string"
},
{
"name": "TargetUserSessionGuid",
"type": "string"
},
{
"name": "TargetUserSessionId",
"type": "string"
},
{
"name": "TargetUserType",
"type": "string"
},
{
"name": "TargetUserUid",
"type": "string"
},
{
"name": "TcpFlagsAck",
"type": "boolean"
},
{
"name": "TcpFlagsFin",
"type": "boolean"
},
{
"name": "TcpFlagsPsh",
"type": "boolean"
},
{
"name": "TcpFlagsRst",
"type": "boolean"
},
{
"name": "TcpFlagsSyn",
"type": "boolean"
},
{
"name": "TcpFlagsUrg",
"type": "boolean"
},
{
"name": "ThreatCategory",
"type": "string"
},
{
"name": "ThreatConfidence",
"type": "int"
},
{
"name": "ThreatField",
"type": "string"
},
{
"name": "ThreatFilePath",
"type": "string"
},
{
"name": "ThreatFirstReportedTime",
"type": "datetime"
},
{
"name": "ThreatFirstReportedTime_d",
"type": "datetime"
},
{
"name": "ThreatId",
"type": "string"
},
{
"name": "ThreatIpAddr",
"type": "string"
},
{
"name": "ThreatIsActive",
"type": "boolean"
},
{
"name": "ThreatLastReportedTime",
"type": "datetime"
},
{
"name": "ThreatLastReportedTime_d",
"type": "datetime"
},
{
"name": "ThreatName",
"type": "string"
},
{
"name": "ThreatOriginalConfidence",
"type": "string"
},
{
"name": "ThreatOriginalRiskLevel",
"type": "string"
},
{
"name": "ThreatOriginalRiskLevel_s",
"type": "string"
},
{
"name": "ThreatRiskLevel",
"type": "int"
},
{
"name": "TimeGenerated",
"type": "datetime"
},
{
"name": "TransactionIdHex",
"type": "string"
},
{
"name": "Type",
"type": "string"
},
{
"name": "Url",
"type": "string"
},
{
"name": "UrlCategory",
"type": "string"
},
{
"name": "UrlOriginal",
"type": "string"
},
{
"name": "ValueType",
"type": "string"
}
]
}
},
"destinations": {
"logAnalytics": [
{
"workspaceResourceId": "[parameters('workspaceResourceId')]",
"name": "ASimWorkspace"
}
]
},
"dataFlows": [
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='AuditEvent'",
"outputStream": "Microsoft-ASimAuditEventLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='Authentication'",
"outputStream": "Microsoft-ASimAuthenticationEventLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='DhcpEvent'",
"outputStream": "Microsoft-ASimDhcpEventLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='Dns' | extend ThreatFirstReportedTime=tostring(ThreatFirstReportedTime), ThreatLastReportedTime=tostring(ThreatLastReportedTime), ThreatOriginalRiskLevel=toint(ThreatOriginalRiskLevel) ",
"outputStream": "Microsoft-ASimDnsActivityLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='FileEvent'",
"outputStream": "Microsoft-ASimFileEventLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='NetworkSession'",
"outputStream": "Microsoft-ASimNetworkSessionLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='ProcessEvent'",
"outputStream": "Microsoft-ASimProcessEventLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='RegistryEvent'",
"outputStream": "Microsoft-ASimRegistryEventLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='UserManagement'",
"outputStream": "Microsoft-ASimUserManagementActivityLogs"
},
{
"streams": [
"[variables('streamName')]"
],
"destinations": [
"ASimWorkspace"
],
"transformKql": "source | where EventSchema=='WebSession'",
"outputStream": "Microsoft-ASimWebSessionLogs"
}
]
}
}
],
"outputs": {
"dataCollectionRuleId": {
"type": "string",
"value": "[reference(resourceId('Microsoft.Insights/dataCollectionRules', parameters('dataCollectionRuleName'))).immutableId]"
},
"streamName": {
"type": "string",
"value": "[variables('streamName')]"
},
"logsIngestionEndpoint": {
"type": "string",
"value": "[reference(resourceId('Microsoft.Insights/dataCollectionRules', parameters('dataCollectionRuleName'))).endpoints.logsIngestion]"
}
}
}Click "Save" at the bottom of the page.
Enter a name for "Data Collection Rule Name" and enter the Workspace Resource ID gathered previously.
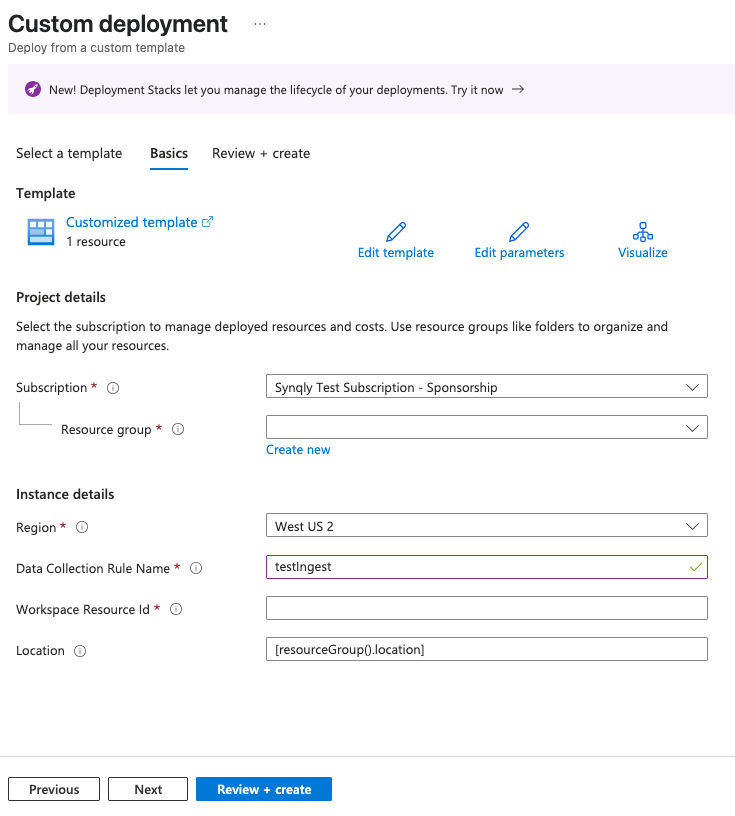
Click "Review + create" and then "Create."
After the deployment is complete, open the 'Outputs' tab and note the Rule ID, Stream Name, and Logs Ingestion Endpoint.
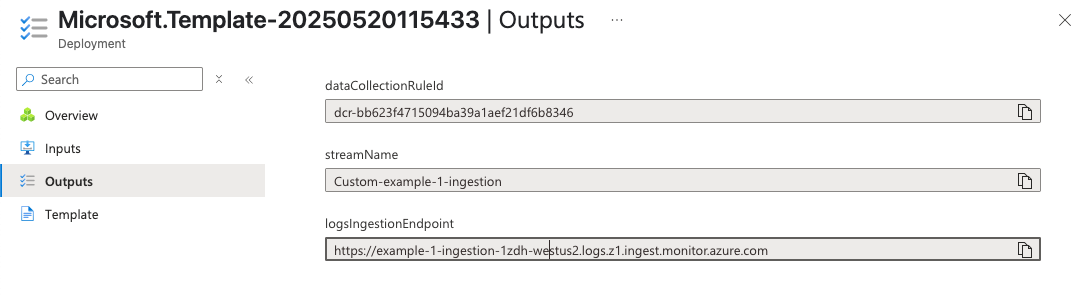
If you do not collect these items from the Outputs tab, you can alternatively gather them from the Data Collection Rule's JSON View.
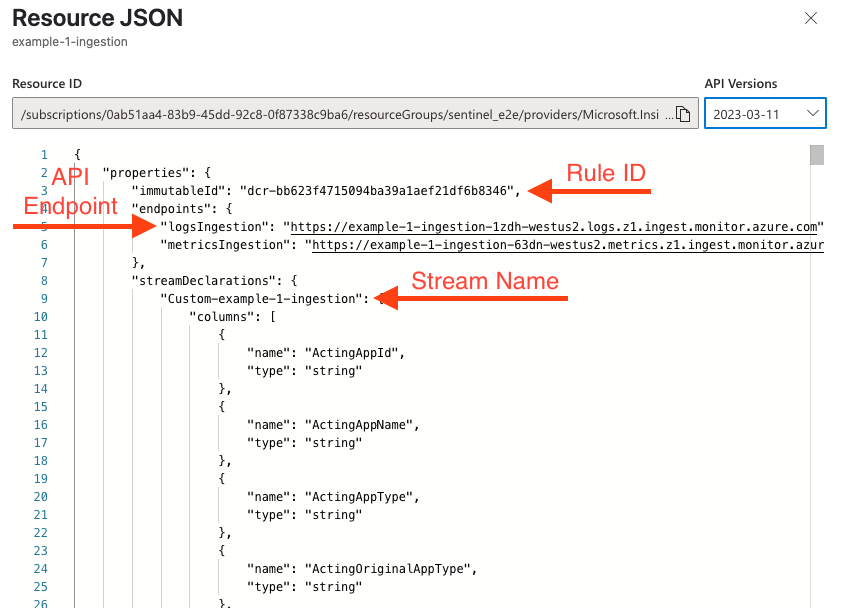
Open the Data Collection Rule and from the Overview tab click the "JSON View" link. Switch the 'API Versions' dropdown to "2023-03-11" or later. Gather your Rule ID, Stream Name, and Logs Ingestion Endpoint from the JSON object as shown.
Finally, we need to add rights for the App we created in Step 1 to write to the new Data Collection Rule. With the Data Collection Rule still open, select "Access Control (IAM)" and then select "+ Add" and "Add role assignment".
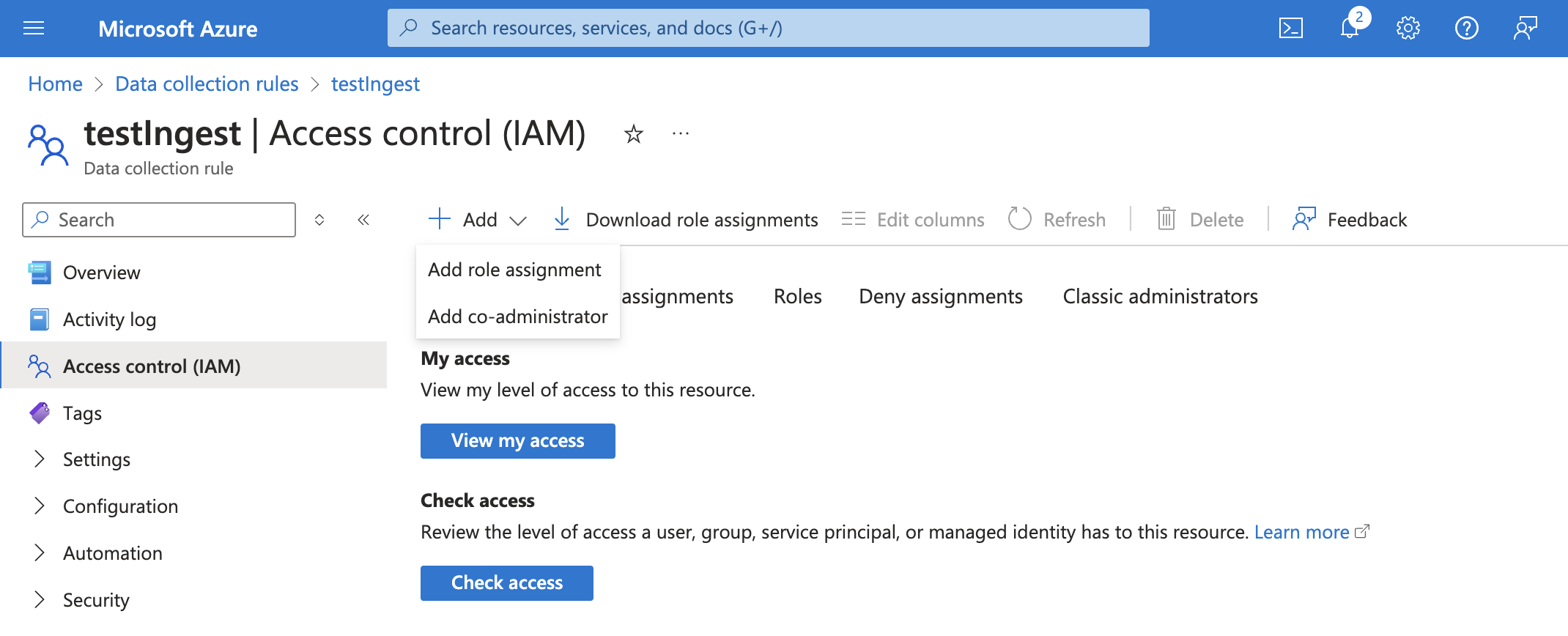
On the next screen, search for "Monitoring Metrics Publisher". Select this role and click on "Next".
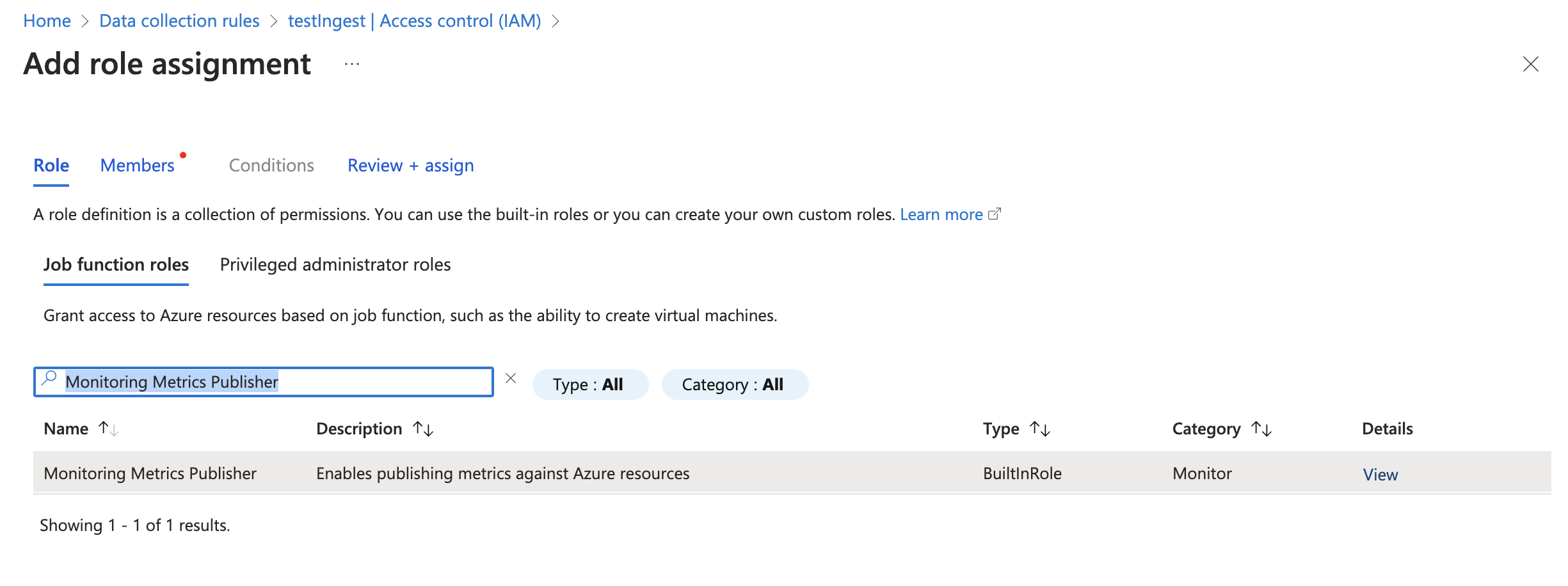
Click on "+ Select members" and add the Application created in the first step. Finish by selecting "Select", then "Review + assign".
Create your integration by supplying all of the values.
URL: This is the Logs Ingestion Endpoint gathered in Step 3
Tenant ID: This is the 'Directory (tenant) ID' gathered in step 1
Client ID: This is the 'Application (client) ID' gathered in step 1
Credential Secret: This is the client secret gathered in step 1.
Rule ID: This is the Rule ID gathered in step 3.
Stream Nam: This is the Stream Name gathered in step 3